Securing Data in Transit Through Any Cloud, Network, or Device
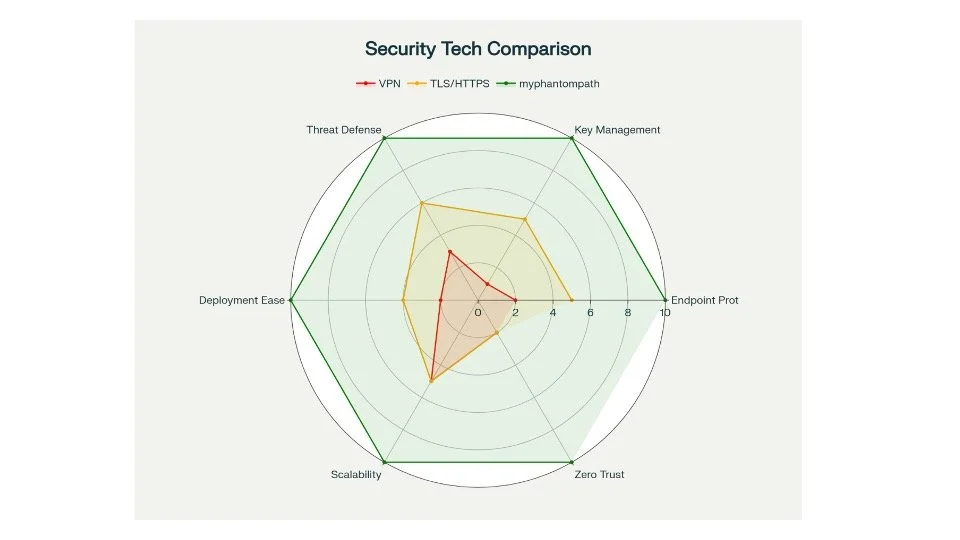
The Defense-in-Depth Reality - myphantompath provides the missing security layer:
1. VPN: Protects network perimeter
2. TLS: Secures web applications
3. myphantompath: Encrypts all endpoint communications with ephemeral keys
VPN and TLS leave critical gaps in endpoint-to-endpoint security, microsegmentation, and ephemeral key management. myphantompath fills these gaps with government-grade technology that provides automated, transparent protection for communications that traditional solutions simply cannot secure—making it essential for comprehensive Zero Trust security architecture, even when layered on existing infrastructure.
myphantompath automates the encryption of traffic between untrusted endpoints across insecure networks, which previously was impossible to secure at scale using with Software as a Service or SDK wrapper for API.
Specializing in Zero Trust Network, Data-In-Transit, and Secure Access Service Edge solutions for enterprise organizations. myphantompath makes the IP address invisible, manages Key Management System (KMS), & Protects Data In Transit at layers 2 & 3.

Our Data Security Mission
myphantompath is based on proven technology developed through a classified US government program. This technology was designed to protect communications that move across untrusted networks like the internet. The US government has been using this technology for more than five years. Now it’s available to commercial partners.

Reduces Enterprise Risk
Uses ephemeral keys and generates new ones each time a connection is established
Sends all data through secure tunnels
Authenticates endpoints prior to establishing connections or exposing resources
Integrates Without Overhead
Easy to deploy, manage, use, and support
Automates certificate and session management
Is transparent to the user and to applications
Lowers Cost
Simplifies key management
Reduces the need for network software and hardware
Creates a highly scalable and efficient infrastructure

The Growing Issue
Cyber threats grow at an increasing pace and undermine the trust of digital communications and data. Challenges and demands continue to evolve, which require innovation to maintain security.
How It Works
myphantompath develops low-cost, lightweight, on-demand encryption technology and licenses it to partners:
For transactional and network security between devices, containers, and services.
As embeddable security components for new or existing solutions.
myphantompath automates the encryption of traffic between untrusted endpoints across insecure networks, which previously was impossible to secure at scale.
myphantompath leverages the computational power of public and private clouds and changes the economics and utility of network layer encryption. You can embed myphantompath to secure data in transit within existing offerings or in new standalone offerings.
Official myphantompath Documents
Brochure
This brochure gives you an overview of myphantompath, the technology, and how it works.
White Paper
This white paper outlines the advantages of myphantompath’s automated, software-defined approach to securing and encrypting data as it transits between endpoints.
Datasheet
This datasheet breaks down the current challenges, and how myphantompath meets them—and beats the.
Get in Touch With Us
If you are interested in getting more information about how you business can leverage myphantompath’s unique technology reach out to our team.